3. The result | |||||||
|
As a result,
the first time
(since you opened your web browser)
you try to access
a document protected via this
Protection setup,
you receive a dialog box like the following 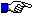
You may try now. When you receive the real dialog box, enter
|
| ||||||
- If the user name and the password are correct,
the http server will
temporarily switch to user profile WEBUSER01 to complete the request- if the request is accepted, the secured page is displayed, and the dialog box is no longer requested (you will always enabled to access this page) until you restart your browser
- if the request is not accepted, an error message is displayed, and the dialog box is no longer requested (you cannot access this page) until you restart your browser
- If the user name and/or the password are not correct
- you receive an error message
- on the next attemp you will receive again this dialog box
